There’s more than one way to measure the success of your content marketing strategy.
Traffic. Lead volume. Revenue. The list of KPIs is long, and it spans the entirety of your funnel.
No matter what you’re focused on, differentiation is essential. If you want someone to read your blog post, you have to say something unique. If you want someone to fill out your form, you have to offer something unique. If you want someone to buy your product, you have to earn and maintain their trust—and one way you can do that is by engaging them with content that they can’t find anywhere else.
A differentiated approach to content marketing is particularly valuable in the cybersecurity world—a world characterized by thousands of companies and dozens of disciplines. Even if you can count on one hand the number of competitors that offer exactly what you offer, chances are there’s a boatload of companies with which you overlap in some way, shape, or form.
Translation: Yours is far from the only content to which your target audience is exposed.
We’re here to help. Using our competitive intelligence software platform, we analyzed more than 2,000 pieces of content—blog posts, podcasts, whitepapers, webinars, etc.—published by cybersecurity companies between March 1, 2021 and August 31, 2021. Based on our findings, we’ve identified two tactics that you can employ to build a more differentiated strategy:
- Repurpose ransomware-focused content across a variety of formats.
- Create sector-specific content.
Let’s discuss each of these tactics in more detail.
1. Repurpose ransomware-focused content across a variety of formats
Given the complexity of the cybersecurity world, we tried to make our content sample as representative as possible. AppSec, MDR, SIEM, threat intelligence, you name it—we analyzed the output of all kinds of different vendors.
Ransomware was one of the few topics where everyone had something to say. Perhaps this is to be expected, given that, in the aftermath of the Colonial Pipeline attack, interest in the subject has reached its highest levels since the spring of 2017 (WannaCry).
Alas, the diversity of voices was not matched by a diversity of media. Of the 192 ransomware-focused content pieces we captured, 131 (68%) were blog posts, 46 (24%) were videos, 8 (4%) were webinars, and 7 (4%) were something else.
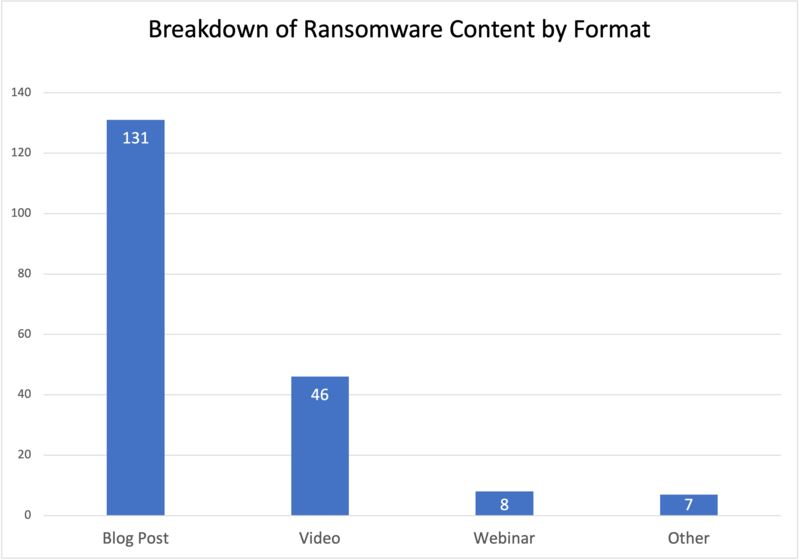
That blog posts are so heavily favored when discussing ransomware is not surprising—nor is it necessarily a bad thing. Blogging has long been an effective content marketing tool for B2B companies, and given the spike in interest picked up by Google, publishing ransomware-related blog posts seems like a sensible way to drive website traffic.
But our data makes something very clear: If your company has a unique perspective on this subject, and you want that perspective to break through the noise of all the other perspectives, then sticking exclusively to blog posts probably isn’t the best idea.
When it comes to ransomware, Tenable’s content strategy is admirably diverse. Between March 1 and August 31, they created blog posts, podcasts, webinars, whitepapers, and YouTube videos. Also notable is the fact that their ransomware-related content has been trending upward:
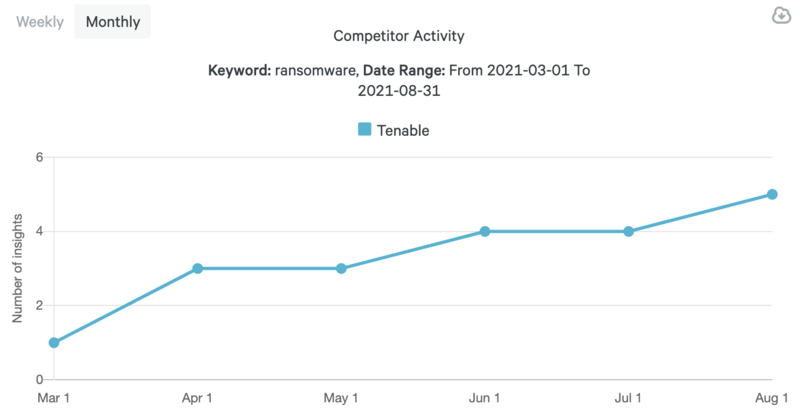
To be clear, we’re not suggesting that ransomware should dominate your content marketing. There are innumerable topics to explore, and depending on which specific niche your company occupies, this particular topic may not even be that important.
Here’s what we are suggesting: If you’re going to create content related to ransomware, developing a diversified approach (a la Tenable) is a smart move. Next time you write a blog post, consider repurposing it into at least one other format—maybe even an infographic, like this one from AT&T Cybersecurity.
2. Create sector-specific content
As you know, security needs can vary dramatically from one sector to another. Whereas manufacturers, for example, are largely concerned with strengthening their defenses as more and more of the production process is connected to the internet, school systems continue to grapple with the vulnerabilities created by remote and hybrid learning environments.
More generally, although a company from Sector A and a company from Sector B may turn to the same vendor, the pain points that compel them to do so—and the use cases they strive to satisfy—are likely not the same.
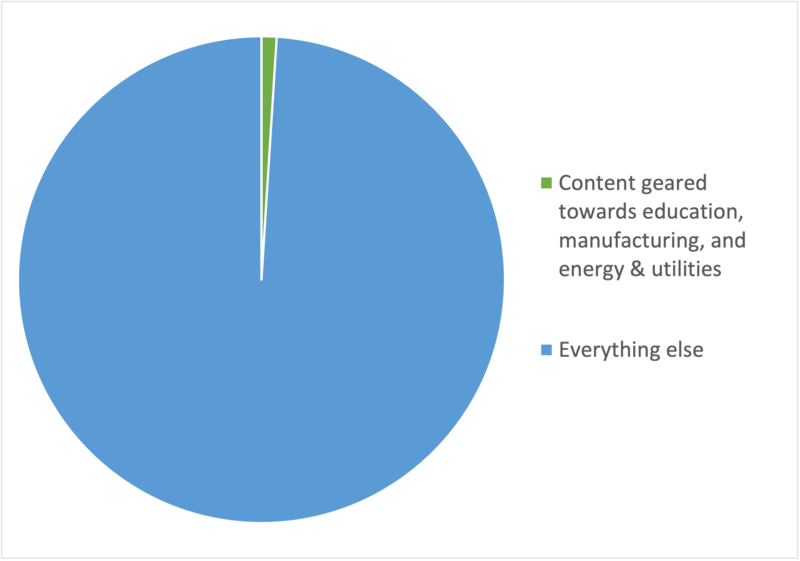
With this in mind, we were surprised to find that sector-specific content is something of a rarity in the cybersecurity world. To see what we mean, let’s narrow our focus to three sectors that are particularly vulnerable to cyber attacks: education, manufacturing, and energy & utilities.
Across our data set of 2,142 content pieces, 13 were geared specifically towards education, 12 were geared specifically towards manufacturing, and—with the exception of some companies’ reactions to the Colonial Pipeline attack—7 were geared specifically towards energy & utilities.
For those of you keeping score at home, a little over 1% of the content we analyzed was targeted towards one of these highly vulnerable sectors. (Also notable is that only AT&T Cybersecurity and IBM Security published at least one piece of content on all three.)
If your company works with clients from any of these sectors—and especially if your company works with clients from all of them—you have an excellent opportunity to further differentiate your content marketing efforts. Showing specific groups of prospects that you (unlike your competitors) understand and empathize with their unique experiences goes a long way towards earning their trust.
Where do you stand in your cybersecurity niche?
Although we hope you got value out of this brief blog post, we recognize that it’s only scratching the surface of what’s going on—from a marketing perspective—in the cybersecurity world.
If you’re eager to get a stronger sense of how you stack up against your closest competitors, check out Crayon’s free competitive landscape report. In a matter of minutes, you can explore a wealth of intel on each rival’s revenue & funding history, website & social reach, and messaging & positioning track record.
Click the banner below to get your free report!

Related Blog Posts
Popular Posts
-
 How to Create a Competitive Matrix (Step-by-Step Guide With Examples + Free Templates)
How to Create a Competitive Matrix (Step-by-Step Guide With Examples + Free Templates)
-
 Sales Battlecards 101: How to Help Your Sellers Leave the Competition In the Dust
Sales Battlecards 101: How to Help Your Sellers Leave the Competition In the Dust
-
 The 8 Free Market Research Tools and Resources You Need to Know
The 8 Free Market Research Tools and Resources You Need to Know
-
 6 Competitive Advantage Examples From the Real World
6 Competitive Advantage Examples From the Real World
-
 How to Measure Product Launch Success: 12 KPIs You Should Be Tracking
How to Measure Product Launch Success: 12 KPIs You Should Be Tracking



.png?width=500&name=Sales%20Enablement-What%20is%20SE_%20(2).png)